If the application does not a choice, then I believe the best choice is to block it. Otherwise, you’ll be greeted with toolbars and other programs. which can be akin to malware and viruses. I believe that the antivirus should let users whitelist without difficulty. Cain and Able which are legitimate and which I frequently use for testing, are typically blocked and difficult to whitelist. I think for home AV, it should be blocked by default and have a flag for allowing it. Corporate AV should be chosen during installation in the management console and include props that are reviewed about every six months. Local backups allow you to save the data in a secret file in the system. Keyloggers for Macs have also appeared in the market and are susceptible to being infected by malware. Get More Softwares From Getintopc
Shadow Keylogger
Password 123
The hardware keyloggers appear like normal USB drives or computers and therefore, the victim won’t be able to identify these trackers as keyloggers. Keyloggers for hardware come with internal memory that stores the keystrokes that were typed or also be part of the form of a module that is integrated into the keyboard. Keyloggers that are based on hardware do not require software installation since they operate on a hardware layer of the computer system. However, keyloggers that are software-based are prevalent and have advanced since their inception. Androids as well as iPhones also have the capability of housing phones keyloggers.
Shadow Keylogger Features
I believe that the antivirus should take the extra step of cautiousness and prevent more of this than not, and especially all keyloggers. The virus is not only transmissible but they are also designed to multiply quickly. Personally, I do not think it’s appropriate to categorize it with Wireshark or an angry ISP scanner. Anyone who is concerned about the type of work the computer is employed for, even when they’re not there. To this end, Shadow Keylogger can provide the tools necessary to keep track of keyboard and screen use. Keylogging can bring certain ethical and trust issues on the line.
Every tool has advantages and disadvantages, and when used properly, could be legally used. A variety of keyloggers for commercial use are available on sale, and a large number of these offer a free trial, which can last from a single day to a full month. The majority of these programs are legal, that are designed to track the use and activities of employees as well as people.
Keyloggers are able to infect computers just as any other type of malware might–by urging the victim to open a browser to download an attachment, open a file or click on a hyperlink. A good example is Trojan keyloggers that are installed on the computers of consumers. These keyloggers are disguised as harmless programs, but they could cause harm when placed on computers. The increasing use of computers in everyday private and business activities on the internet has made keylogging a crucial issue that everyone must know about. If a keylogger is used for legitimate motives or for nefarious reasons it is crucial to be aware of the tools.
They could also be downloaded from an authentic website but could be infected and exploit vulnerabilities or download malicious drive-by files. Keyloggers for software are applications that track every stroke that is made by the user’s keyboard. Keyloggers remotely are utilized to monitor computers from an alternate place.
Always look in the Downloads folder before installing an antivirus program that is reliable. Received strange notifications or messages and the phone’s unusual behavior may be indicators to have the phone examined.
How to Get Shadow Keylogger for Free
To eliminate keyloggers, you must delete the activity trackers, or deinstall these programs. Find the keylogger’s name to learn how to remove the malware. Restarting the computer and uninstalling the program using Safe Mode may do the trick. The anti-logger software is created to protect keystrokes by searching for and eliminating known loggers and flagging any unusual keylogging-like behaviors on computers. Keystroke logging consists of recording the keys that are pressed on the keyboard.
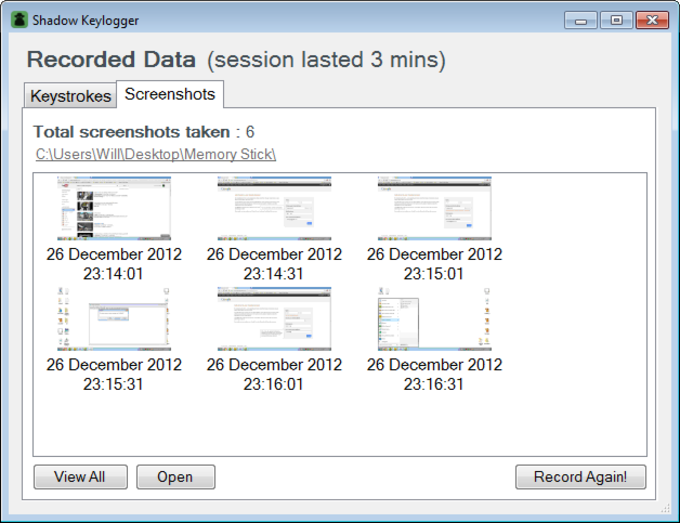
Record, save, and retrieve recorded data from keyboards as well as the monitor of your PC. The powerful single-click deployment feature is able to be configured to run immediately from memory sticks, or upon starting up. A User Agent can be described as a small text that internet browsers and other programs transmit to signal their identity with the webserver. Here, you will find blog tips reviews and new SEO strategies. In short, treat it as PUPS and block the site, but make it easier for admins to add whitelists.
The file was created in 2013, but the detection rate for Virus Total was 30/54. That’s just a little over 50 percent. It seems like it, however, several well-known vendors consider this a valid keylogger tool comparable to Wireshark.
Due to the capabilities of keyloggers they have, it is important to be cautious prior to downloading any files, even from trusted sources and sites. Shadow Keylogger provides a no-cost basic and secure keylogger for Windows that allows you to record the keyboard and screen activities in secret.
Shadow Keylogger System Requirements
- Operating System: Windows Vista/7/8/8.1/10
- Memory (RAM): 1 GB of RAM required.
- Hard Disk Space: 120 MB of free space required.
- Processor: Intel Pentium 4 or later.
