We explored ways to replace strings along with other strategies to create a custom Mimikatz-specific binary. We discovered that Mimikatz’s detection is reduced to about 1/3 of the vendors using the most obvious commonly used strings. However, this could be further reduced by adding more strings. Other methods, such as API import concealing could reduce the rate of detection even more. Get More Softwares From Getintopc
Mimikatz
Password 123
Tickets /export – relies on reading from Kerberos ticket memory. It doesn’t impose any restrictions on exporting keys as well as other commands. Pass-the-Ticket Kerberos System is a network-based authentication protocol that is based on tickets, which allows nodes to communicate with each other via a network that is not secure to validate their identities with one another in a secure manner. Mimikatz has the ability to get tickets through the account of the user and then use them to login into the system under the user’s name. Pass-the-hash — NTLM includes hashes that are used to get passwords. This system aims to allow users to use passwords repeatedly without having to use the same hash repeatedly. Customers can access your services online without passwords and expensive SMS costs.
Mimikatz Features
Through Nevis’ Authentication Cloud it is possible to give your customers the best security as well as a pleasant user experience in a matter of minutes. Secure your company from data breaches that are related to passwords as well as cyberattacks by using Keeper’s strong password security solution. The research shows that 81 percent of data breaches are caused by inadequate and stolen passwords. You can be inspired by a Phrase article on PEzor the design and implementation of PEzor An open-source PE Packer. Shellcode Injection, with Syscall Inlining as well as User-Land Hooks removal and making the Generated Executable polymorphic in order to avoid Trivial Signatures, and more. If you’re still wanting to go further and attempt to achieve FUD, you could achieve more. You can substitute the names with functions by using both lower and uppercase characters.
This tutorial from Mimikatz is meant for a brief introduction to the tool. It is essential to understand the way that Mimikatz operates in real-time and how simple it is to create vulnerabilities to systems for novice attackers. The login passwords command retrieves a user ID and password for login users as well as those who recently signed in to the system in question. The simplest and most efficient command is one that takes plaintext passwords, then lists these on the console, and then writes them into the log files.
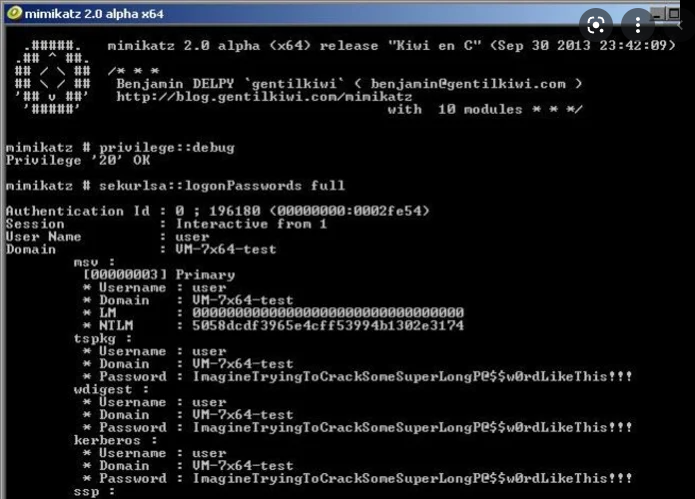
The most common format used to issue commands is to type in the command’s module, followed by two colons, and then the command’s name. It is possible to use multiple commands at a single time however, any commands that contain spaces must be marked off by quotation marks.
If you’ve ever tried downloading a Mimikatz release that has AV enabled it was evident that it isn’t possible since each release is marked as AV-incompatible. It is entirely possible as today, attackers are using Mimikatz as well as other Open Source projects in real-world instances. I’m sure that Mimikatz is one of the most popular programs to retrieve identities from the LSASS procedure and the same database. It can also execute passes through hash attacks as well as decrypt DPAPI secrets, and much more. A good but not complete overview of all the features available is available at ADSecurity.org and in the Mimikatz Wiki. We either alter all function names using upper and lower case or we modify the name completely.
To make sure that only the most well-known Mimikatz indicators are updated in our replacement script, we’ve included most names of subfunctions in the replacement script. The sekurlsa module also includes commands that extract Kerberos credentials as well as encryption keys. It is also able to perform a pass-the-hash attack with the credentials Mimikatz obtains. The best source for Mimikatz is on Mimikatz’s Mimikatz GitHub website, which allows you to obtain Mimikatz source code. Mimikatz sources code. Binaries that have been precompiled for Windows are also available on the Mimikatz GitHub page. Mimikatz makes use of administrator rights in Windows to display passwords for currently registered users in plain text.
How to Get Mimikatz for Free
In addition and scan the virtual machine’s passwords. The laws regarding the application of this software differ between countries. An attacker is able to utilize this key repeatedly to impersonate users. Secure, password-free proximity login for computers, Macs sites, desktop apps, as well as websites. Wireless 2FA, hands-free, and password manager with active proximity detection. IT administrators can allow users to log in to their sites and computers using a physical key, either via touch, automatically, or by… If your business is using cloud-based database providers it’s essential to stay up-to-date with security.
The Win32flavor software cannot use 64 bits processor memory, however, it is able to open 32 bits minidumps within Windows 64 bit. It is highly likely that this program is malicious or has undesirable software that is bundled with it. It’s a sign that harmless software is flagged incorrectly as malicious because of an unwieldy algorithm or detection signature used by antivirus software.
The software could be harmful or could include unwanted software that is bundled. In this article, we analyzed Mimikatz as well as the places and how it could be used and explained the reasons why it could be beneficial and risky if it is used by a malicious person. We’ve seen the best way to set it up on Windows and have also reviewed the basic commands that are used to find the security of sensitive information. Purge – is a cleaning of all tickets, as well as numerous other commands.
Certain operations require administrators’ privileges or SYSTEMtokens, so take note of UAC that is available in the Vista version. Our Support teams are comprised of skilled Linux specialists and System administrators with a deep understanding of various web hosting technology particularly those covered in the article. Module Crypto is a module that can be utilized to integrate CryptoAPI functions.
The Future of Tech Commission wants the federal government to start an integrated effort to address issues related to data privacy … Cloud-native technology from the startup could be incorporated into the Juniper’s … Learn about three main multi-tenancy security issues and ways to solve them, including the lack of visibility, and privilege overallocation…
Mimikatz System Requirements
- Operating System: Windows XP/Vista/7/8/8.1/10.
- Memory (RAM): 1 GB of RAM required.
- Hard Disk Space: 100 MB of free space required.
- Processor: Intel Dual Core processor or later.
